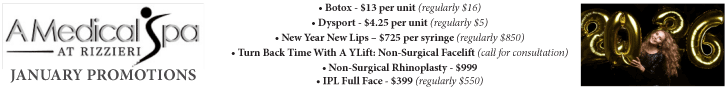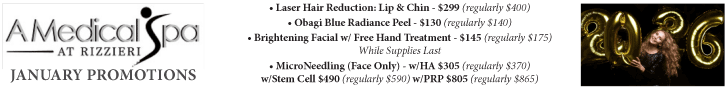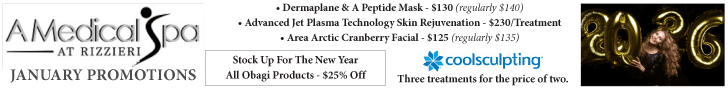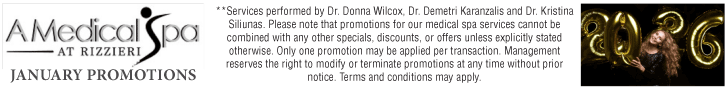
Gone Phishin’

Evolution is key to survival, ensuring environmental adaptation and guaranteeing another generation will carry on. Whether it’s plants and animals, languages and societal norms, or living species and the tools they use, everything has to grow alongside the context or culture it calls home.
Unfortunately, the same goes for more nefarious entities. Companies, businesses and employees eventually get wise to the seemingly infinite ways bad actors and cybercriminals dispatch their phishing tactics, online scams and other methods of finding a vulnerable security lapse for malware to gain access to well-guarded, sensitive data—which means those methods have adapted to lower everyone’s guard in novel and unexpected ways.
“People, for the most part, can recognize all the things that have made us stop in our tracks and say, ‘Wait a minute, that doesn’t seem right’—that’s why we haven’t seen people fall for the Nigerian Prince scam for a long time,” says Russ Abdrakhmanov, owner of the Cherry Hill-based IT provider neKey. “One thing to look out for now is if there’s an emotional component to it, if it’s trying to play with your emotions to put you in an automated mode. Another thing is urgency, if it’s trying to get you to click on their link right now.”
That emotional entrapment is commonly defined as “social engineering.” It’s deliberately manipulative, designed to subvert logical thought by eliciting an impulsive, emotional reaction triggered by a sense of urgency or obligation.
But it’s far from the only trick cybercriminals and other bad actors have up their sleeves to bilk companies and their unsuspecting team members out of their hard-earned money, bypass their security systems, and gain access to sensitive personal or financial data.
As scammers’ sophistication has had to try and outsmart the general population, once seemingly impenetrable safeguards are no longer a sure bet. Mac users have long since thought their devices to be impervious to infiltration, which is no longer the case; similarly, you can’t always be sure that’s a friend or a colleague calling you. Things like AI programs that can imitate a familiar voice with eerie accuracy after being fed only a few sentences of input or cybercriminals pretending to call on behalf of a wholly innocuous organization are among those high-tech Trojan horses bamboozling even the most vigilant and untrusting targets with the way their urgency elicits a response.
“Some of the newest phishing scams we’re seeing are ‘vishing,’ which is when somebody tries to use the phone as a mechanism of phishing, like when you get a call from some foreign person trying to impersonate a legitimate company,” says Tapan Soni, a cybersecurity professor at Rowan University who also works in the industry. “Usually, the goal with these is to try and get you to sign up for something or scope out the landscape to get more information about you because people divulge a lot of information without realizing it.”
But catching targets off-guard with unconventional tactics masquerading as a routine professional experience or interaction can be just as effective. Abdrakhmanov notes that while “the future of scams is deep-fakes,” he’s not seen a lot of chatter or awareness about a growing LinkedIn scam where an individual is invited to apply for a job, submits to a seemingly legitimate and in-depth interview process, and then is offered a job through an email link that’s actually malware in disguise.
It works on multiple levels, he notes, because people are reluctant to admit that looking for a new job is what led to the security breach in the first place, and they’re embarrassed to be the one who left the door wide open in the first place.
The advent of “smishing”—or phishing scams conducted over SMS text messages, often under the guise of an attempted package delivery or a notice about your account activity on PayPal or Amazon—is a fairly modern tactic, too.
One thing people can do, especially if they’re on a desktop or laptop, is hover their cursor over a link to ensure that its destination is safe and going where the accompanying text indicates, Soni advises. Beyond that, you can reduce your chances of falling victim to virtual scams by keeping an eye out for the unusual, messy formatting that’s still one of the most obvious telltale giveaways that a message came from a malicious source.
He adds that two other strategies can help minimize the possibility that you or your team are blindsided by scammers: Slow down and really digest what an email is asking from you before engaging with it; and understand that if it seems too good to be true, it probably is.
Thinking first and acting later is especially effective because, as Abdrakhmanov points out, if people want money from you, they’ll be persistent in their outreach and will get back to you. “If you’re not sure about something, sleep on it,” he advises. “Don’t get emotional, don’t fall for the urgency.”
As far as cybersecurity professionals are concerned, dealing with a hack, phishing scam or security failure is not a matter of it but when, which is why it’s imperative to have not only a plan in place but also practice regular pressure-testing drills emulating a real-world worst-case scenario. Soni observes that since “scammers rely on you not paying attention,” both ongoing educational and mindful proactive awareness are two of the best tools in your arsenal to defend your company, reputation and financial well-being.
There are an array of cybersecurity-awareness programs and similar educational tools and services on the market. They include everything from videos that employees have to prove that they’ve both watched and learned from, to programs that emulate a popular phishing tactic by sending out an email with a link that, should someone in your company click on it, will notify that team member that they’ve fallen for a potentially dangerous scam.
As it is difficult to anticipate or even conceptualize just how disastrous or extensive a successful scam can be, staying educated about modern scamming trends can help employees understand just how much is on the line if they let complacency turn them into your security network’s most vulnerable point of ingress.
“No matter how many different cybersecurity controls that an organization has, any of your employees are your most powerful and weakest links,” Soni says. “You can have the greatest firewalls, the greatest intrusion-prevention systems on the planet, but if you have somebody just opening the doors for a malicious actor, it’s not going to do you any good.”
When that successful scam zeroes in on your company, that’s the time for urgent action. Neutralizing the threat as quickly as possible and being transparent in notifying your clients of the full extent of the damage are crucial first steps.
“In general, there’s a lot of tools out there and most, if not all, email security systems have those tools built in where you can triage and contain these kinds of threats very, very quickly,” says Soni. “But, regaining trust is very difficult. That’s something upper leadership has a say in, if they want to contact their end users and third-party users and say ‘Hey, we’ve been hit, and something might have happened.’ But it’s really based on the scenario.”
Abdrakhmanov agrees that reestablishing trust and restoring your reputation is an uphill battle post-hack. That’s why he urges companies big and small to be vigilant, be educated and be smart in their online usage.
“Phishing is just the tip of the iceberg—it’s the gate into your network,” he says. “You don’t really know who’s calling you. You don’t really know who that email is from. You don’t really know who that text is from. Keep those things in your head as basic principles and always remain alert, and that will go a very long way in protecting you at home and at work.”
advertisement

Author: Madeleine Maccar
Archives
No Matter Who Is The Eagles Offensive Coordinator – Two Other Things Must Change
The All-South Jersey Girls’ Soccer Team
Looking at the Rugged Olympic Conference American Division Boys’ Basketball Race
South Jersey vs the Shore Features Some of the Top Girls Basketball Teams In the State
Time for Change
Temper Expectations
Top CEOs & CFOs 2026
The All-South Jersey Boys’ Soccer Team
Eagles Warts Exposed In Playoff Ouster
Eagles Hope Resting Regulars In Season Finale Won’t Be Costly
Looking At Some South Jersey Boys’ Basketball Teams that Showed Well During Holiday Tournaments
Recapping South Jersey Girls Basketball Teams During Holiday Tournaments
Eagles D In A Form As Postseason Nears
Winslow Township Ends Another Season As South Jersey’s Consensus No. 1 Football Team
Another Big South Jersey H.S. Field Hockey Season
More...